Well well well. After all my downvotes, you find yourself back here. Maybe I know a couple'a three things after all, huh? No hard feelings. So, you might want to run a lightweight version of K8s on a cheap but mighty server, and have trouble finding documentation to help you with that? No worries, I got you! This guide walks through installing K3s, the lightweight Kubernetes distro, on Hetzner Cloud.
Prerequisites
- Hetzner Cloud Account: Set up a server with Ubuntu (preferably a fresh install).
- SSH Access: Ensure you have SSH access to the server.
Step 1: SSH into Your Hetzner Server
Start by connecting to your server via SSH:
ssh -i ~/path/to/yourkey.ssh root@<your-server-ip>
Replace <your-server-ip> with the actual IP address of your Hetzner server.
I used Ubuntu, so before I installed K3s, I ran
sudo apt update
Step 2: Install K3s
Run the following command to install K3s directly:
curl -sfL https://get.k3s.io | sh -
This script installs K3s with default settings, setting up a single-node K3s cluster.
Step 3: Check the Installation
After installation, verify that K3s is running and configured correctly.
- Check if K3s is running correctly and verify Node Status:
sudo systemctl status k3s
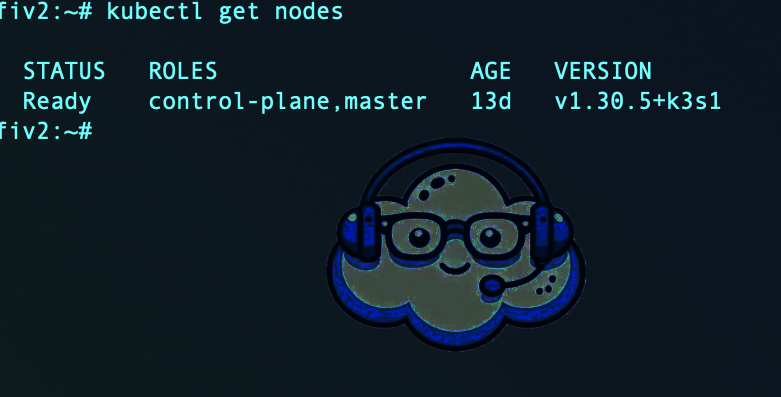
kubectl get nodes
This second command should list your server as a Kubernetes node with the status Ready.
- Check All Pods:
To see all system pods and ensure everything is running as expected, use:
kubectl get pods -A
Step 4: Access K3s Cluster Configuration
To access K3s on your local machine, copy the K3s kubeconfig file.
- Locate the Kubeconfig on your server:
cat /etc/rancher/k3s/k3s.yaml
- Copy the Configuration File to your local machine and update the server IP to the Hetzner server IP in the k3s.yaml file and then apply it. Alternatively, you can configure kubectl to use it directly:
export KUBECONFIG=/etc/rancher/k3s/k3s.yaml
Step 5: Finalize Installation and Security Adjustments
- Disable sudo for Kubernetes Commands:
If you need permissions to manage Kubernetes without sudo, modify the K3s kubeconfig as follows:
chmod 644 /etc/rancher/k3s/k3s.yaml
- Enable Access:
Set up firewall rules or security groups on Hetzner if you need external access to Kubernetes services. Keep port 80 and 443 open for HTTP/HTTPS traffic, Make sure you enable port 22 from your local IP address for maximum security (if you're using a VPN, use that address, don't get locked out, I've been there before!)
Your K3s cluster is now up and running on Hetzner Cloud with Ubuntu! You can manage it using kubectl commands from either your server or by configuring access from your local machine. Next let's set up GitOps with Argo.
Step 1: Apply the Argo CD Installation Manifest
Argo CD provides an installation YAML manifest that can be directly applied to your Kubernetes cluster.
Install Argo CD:
Run the following command to install Argo CD in the argocd namespace:
kubectl create namespace argocd
kubectl apply -n argocd -f https://raw.githubusercontent.com/argoproj/argo-cd/stable/manifests/install.yaml
Verify Argo CD Components:
Check that all Argo CD components are up and running in the argocd namespace:
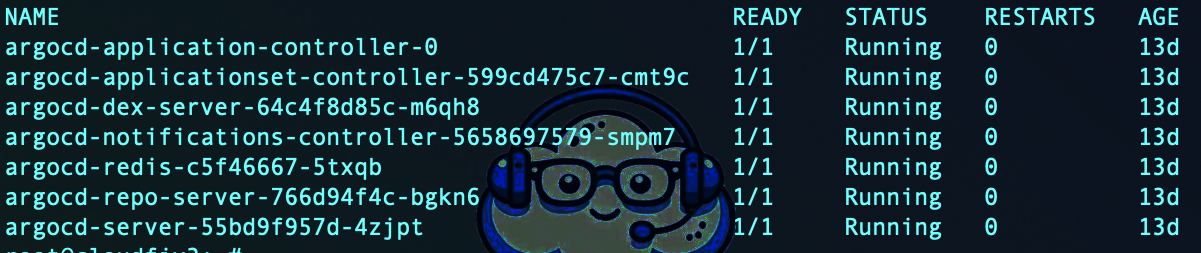
kubectl get pods -n argocd
All pods (e.g., argocd-server, argocd-repo-server, argocd-application-controller) should show the status Running.
Expose Argo CD Server (Optional for External Access)
If you need external access to the Argo CD server, expose it through a LoadBalancer or NodePort. Here’s how to expose it using NodePort, if you're doing this in the cloud, deploying a load balancer might incur an additional cost, so NodePort might be the simplest solution:
kubectl patch svc argocd-server -n argocd -p '{"spec": {"type": "NodePort"}}'
To retrieve the NodePort and access the Argo CD UI:
kubectl get svc argocd-server -n argocd
The output will show the assigned port (e.g., 32000), which you can use with your server’s IP (e.g., http://<server-ip>:<NodePort>).
Retrieve Initial Admin Password
The initial password for the admin user is stored as a secret in Kubernetes. Run the following command to retrieve it:
kubectl get secret argocd-initial-admin-secret -n argocd -o jsonpath="{.data.password}" | base64 -d
Copy this password for the first login.
Access the Argo CD UI
- Open your browser and go to the Argo CD UI using the NodePort URL (http://<server-ip>:<NodePort>).
- Log in with the username admin and the password you retrieved in Step 3.

Update Argo CD Admin Password (Recommended)
Once logged in, it’s recommended to change the default admin password for security.
- Go to Settings in the Argo CD UI.
- Update the password for the admin user.
Configure Argo CD for GitOps
- Connect a Git Repository: In Argo CD, you can connect to your Git repository to set up a GitOps workflow.
- Deploy Applications: Set up Argo CD applications by pointing them to paths in your Git repository containing Kubernetes manifests or Helm charts.
Create a folder (e.g., argo-cd) in your Git repository, and within it, place the Argo CD manifests, including configurations for namespaces, roles, etc. Ensure you have the argocd namespace manifest and any custom configurations saved here.
Step 2: Define the Argo CD Application YAML for Self-Management
This Application YAML tells Argo CD to monitor its own configuration in the Git repository.
Create a YAML file named argo-cd-application.yaml with the following content, replacing <repo-url> with the URL of your Git repository and <path-to-argocd-folder> with the path within the repository:
apiVersion: argoproj.io/v1alpha1
kind: Application
metadata:
name: argocd
namespace: argocd
spec:
project: default
source:
repoURL: '<repo-url>'
targetRevision: HEAD
path: '<path-to-argocd-folder>'
destination:
server: https://kubernetes.default.svc
namespace: argocd
syncPolicy:
automated:
prune: true
selfHeal: true
prune: true: Allows Argo CD to remove resources no longer tracked in Git.
selfHeal: true: Enables Argo CD to reconcile automatically when out of sync.
Apply the Self-Management Application to Argo CD
- Push argo-cd-application.yaml to your Git repository.
- Apply this configuration directly to Argo CD by running:
kubectl apply -f argo-cd-application.yaml -n argocd
Verify Self-Management
- Open the Argo CD UI and check the Applications list.
- You should see argocd listed as an application within Argo CD.
- Argo CD will now monitor its configuration in the specified Git repository path, applying changes automatically.
And that's it! Best practice is to do everything through your chosen Git repo, and have Argo reconcile any changes by versioning the manifest of the deployments you want to update.
Follow me on that social media site I refuse to call by the most edgelord letter in the alphabet and check out my latest Lofi study videos






